
Five Cyber Insurance Considerations
When you read the news or simply turn on the television, cyber security is a much bigger problem today than…

Cyber Security Recap: 2022
The passing of another year provides a perfect opportunity to reflect. And, because 2023 marks the 50th anniversary of the…

Why Business Continuity Makes Sense for SMBs
Did you know that approximately 40 to 60 percent of small businesses that experience a total shutdown of operations never…

NextGen Managed Services: Break Free from Break/Fix
“We’ll just fix it when it breaks!” Now there’s a mindset which looks completely out of place in a whole…

How I Got Hacked
Written by Christopher Dean of Citon/ACP My teenage son plays varsity soccer for his local high school team. As fans…

Understanding the Cost of Downtime
Of all the different factors that can cause system downtime, including human error and natural disasters, ransomware sits atop the…

How Your Business Can Recover Quickly from Any Disaster
Far too many people rely solely on hope when it comes to avoiding a disaster that has the potential to…

Defining Managed Services
Whether you’re plagued with persistent network problems, such as security vulnerabilities, poor performance, and a barrage of support requests, or…

Network Access Control for a Zero Trust Age
Previously, we’ve written about the zero trust network security framework and separately, about network access control (NAC). But how do…
Securing Your IoT Devices
What is IoT (Internet of Things)? The Internet of Things (IoT) describes the network of physical objects, hence the use…

The Importance of Network Access Control (NAC)
Security teams are facing challenges when it comes to maintaining visibility across remote, in-office, and hybrid work environments as business…

Cloud Security & How It Impacts Your Insurance Policy
According to a 2022 Cyber Threat Report released by SonicWall, ransomware is up 232% since 2019. For most organizations that…

Discovering the Latest Enhancements to HPE GreenLake (Pt. 2)
Last week we gave an overview of all the upcoming enhancements that were announced at HPE Discover 2022 in June.…

Discovering the Latest Enhancements to HPE GreenLake (Pt. 1)
GreenLake, HPE’s flagship offering, provides organizations the ability to modernize all their applications and data. A slew of announcements so…

HPE GreenLake for VDI: A “Best of ALL Worlds” Approach?
Virtual desktop infrastructure (VDI) is a desktop virtualization technology whereby a desktop operating system (typically Microsoft Windows) runs and is…

HPE GreenLake-Delivering a Paradigm Shift With IT Consumption Model
Talk on the topic of public cloud vs. on-premises IT and the pros and cons of each has been intensifying…

Uncovering Your Strongest Defense Against Gun Threats
In order to mitigate threats and protect assets, security professionals have increasingly deployed a layered security strategy. The common “5…

Why the Cloud Makes Sense for Physical Security
Leveraging the cloud for physical security can result in a plethora of benefits. For instance, video footage in the cloud…

Is Your Business Protected? Use This Office Physical Security Audit to Find Out!
Burglars, breaches, and intruders all pose a threat to the safety of your workplace. Developing a clear understanding of the…

Physical Security Fundamentals
Lately, much of the customer outreach, consulting, and solutions provided by ACP, CCCP, and Citon has been focused on cyber…

Chrome, Safari, and Edge: A Comparison of the Cyber Security Built Into Our Default Browsers
The internet is a pervasive part of everyday life for nearly everyone now. It’s unavoidable (although there are times we…

What to Do When You Are the Victim of a Cyber Security Attack
The world is more connected than ever leading to more freedom when it comes to how we get our work…
Never Trust and ALWAYS Verify (and Verify, and Verify)
Although the phrase, “Trust, but verify” is frequently attributed to former US President Ronald Reagan, who used it on multiple…

NFTs: Tips, Tricks, and Terms to Know
NFTs have been all the rage for the better part of the last year. Whether you’re already convinced that NFTs…

Are NFTs Here to Stay?
NFTs, recently named the 2021 word of the year by Collins Dictionary, will likely stick around and continue to play…

Factors to Consider Before Investing in NFTs
The current mania surrounding NFT’s will surely raise plenty of eyebrows. Before you dive headfirst into investing, be aware that…

What Are NFTs and How Do They Hold Value?
Last month, millions of Americans sat down to watch Super Bowl 56, and even more tuned in to watch the…

Expand Your Knowledge on Microsoft Security
Microsoft 365, as a service, contains numerous administration portals, options, and configuration settings centered on security. Azure Active Directory for…

Understanding Microsoft Intune
Mobile device management (MDM) and mobile application management (MAM) are the focus of the cloud-based service Microsoft Intune. As part…

Microsoft NCE Changes
*Update: Microsoft has extended the March 1st deadline for renewals to June 30th, 2022 for Legacy CSP. You can renew…
Cyber Security Recap: 2021
With 2021 in the rearview mirror, we are given the opportunity to recap the cyber security trends and events it…

Cyber Security Framework: Breaking Down the Acronyms
MDR. EPP. EDR. XDR. The list goes on for acronyms relating to cyber security. As hackers and internet crimes become…

Human Error: Your Weakest Link in the Fight Against Bad Actors
The unintentional action, or lack of action, by users that results in the cause, spreading or allowing of a security…

Securing Your Top Threat Vector: Email
Email will consistently find itself as a top threat vector since it’s a staple in the workplace that everyone uses.…

Understanding the Chip Shortage
Microchips play a much more critical part in our lives than you may have ever imagined. Our phones, computers and…

Hewlett Packard Enterprise strengthens GreenLake offering with breakthrough analytics and data protection cloud services
HPE announced Sept. 28 its latest advances toward cloud offerings. The updates can be broken down into three subset categories:…

Collaboration in the Dynamic Work Environment
Once you have deciphered what platform best fits your organization’s needs you will need to figure out the logistics of…
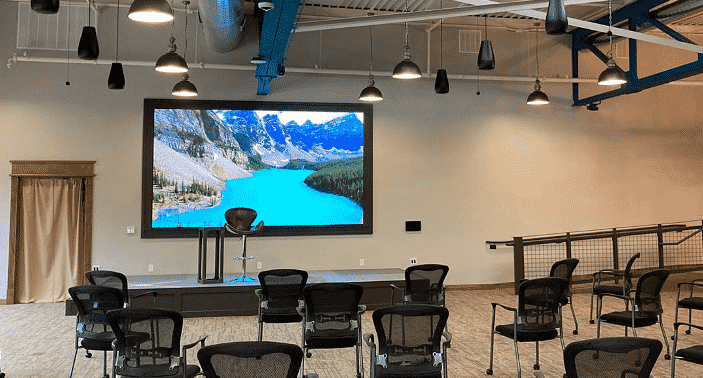
Improved Training Experience Coming to InitiativeOne from Daktronics
New 1.9-millimeter LED video wall to aid with executive training BROOKINGS, S.D. – Sept. 23, 2021 – To enhance their…

Things To Consider When Deciding Between Popular Video Conferencing Platforms
Video conferencing has become a staple in the modern workplace as organizations are tasked with giving employees the ability to…

Deploy Layered Protection with Multi-Factor Authentication
Targets such as physical locations, computing devices, networks or databases become more difficult for unauthorized people to access thanks to…

Types of Cyber Attacks to Watch Out For
Cyber security is at the forefront of many businesses’ minds. With attacks constantly adapting and evolving you must always be…

15 Ways to Protect Your Business From a Cyber Attack
No matter what size your organization is, what line of business you’re in, or who you serve, bad actors are targeting…

Why Apple™ Makes Sense for Your Organization
Apple’s™ reputation of going the extra mile will pay financial dividends for your business. Durable materials are used in the…

Apple™ Business Manager: Deployment Made Easy
Deployment of Apple™ devices has never been easier thanks Apple Business Manager. This web-based portal provides IT with the luxury of…

Embracing an Employee Choice Program
Expansion of how companies embrace Apple™ in the workplace is occurring everywhere. It’s critical that employees are provided with the best tools…

Apple™’s M1 Chip Sets a New Standard
Unlike previous chips powering Apple’s devices built on the x86 architecture, the new Apple Silicon M1 deploys an ARM-based architecture.…

Increasing School Safety Through the Power of a HALO
Ingram Micro Success Story Vaping is an epidemic health experts are not talking about much these days but remains a…

Simplify the World of Work with Unified Communications
Digital transformation has spurred a brand-new world of evolving technology. Work has become boundaryless with employees no longer refined to…
Camera Corner Connecting Point Named Vertiv 2020 Central United States Partner of the Year
Green Bay, Wis. [May 11, 2021] – Camera Corner Connecting Point, announced today that it has been named the Vertiv…

Enhance Your Microsoft Teams Experience with 8×8 Voice
Take your Microsoft Teams experience to the next level with Direct Routing from 8x8. Organizations around the world use Teams…

What to Consider When Deciding on a Phone System
Phone systems (VoIP) can be daunting to evaluate. We are here to make that process simple and easy for you…

Free your IT Staff with Managed Help Desk Services
Not every support issue can be called a catastrophe…until it prevents you or your team from being able to do your job. Outsourcing your…

The 5 Worst Data Breaches of All Time
No matter what type of information is being accessed, all data breaches are scary because they involve the release of…

Defining Managed Services
Whether you’re plagued with persistent network problems, such as security vulnerabilities, poor performance, and a barrage of support requests, or…

The Case for Co-Managed Services with NetAssist
No more frustrations and wasted time on technology issues. The flexible co-managed service offerings of ACP/CCCP's NetAssist division relieve your…

So You Went Remote, What Next?
While there seemingly appears to be a light at the end of the COVID-19 tunnel, there are sure to be lasting…

How to Implement a Modern Workplace Initiative
The modern workplace can be described as a fluid and casual environment where a work-life balance is prioritized. The traditional…

Endpoint Protection Has Become a Priority
Endpoints have ascended to the forefront of security information. If you are curious what an endpoint is, simply put, it’s…

The Growing Need for Modern Collaboration
The days where everyone always reports to an in-person physical workplace, such as a company headquarters or office, seem to be behind us. The typical nine-to-five schedules have become a rarity.…

“New Normal” Webinar Recap
During our regional cyber threat briefing webinar earlier this week we had an FBI special agent and leaders in the…

Why Choose ACP CreativIT/Camera Corner Connecting Point for Cyber Security?
No matter what size your organization is, what line of business you’re in, or who you serve, hackers are targeting…

Modernizing Security with the Enforcement of CMMC Requirements
An unprecedented average of 1,300 complaints are fielded daily by the FBI regarding cyber security concerns. When the dust settled…

What Threats Litter the Cyber Security Landscape in 2021?
There is no arguing cyber security threats are on the rise. The COVID-19 pandemic has given hackers new opportunities and…
Technology Trends To Expect In 2021
The last six months has led to more digital transformation produced than the last decade due to the unpredictable COVID-19 pandemic and the…

Microsoft Reinforces The Move Towards Subscription-Based Microsoft 365
Last week Microsoft reminded customers that Office 2010 and Office 2016 for Mac have received their final security updates. With…

Flexible Co-Managed Service Offerings From NetAssist Relieve Your Day-To-Day IT Worries!
No more frustrations and wasted time on technology issues. The flexible co-managed service offerings of NetAssist relieve your day-to-day IT…
Pure Storage Helps You Innovate With A Modern Data Experience
Take advantage of your opportunity to get a modern data experience from the industry’s leading all-flash storage innovator: Pure Storage.…

ACP CreativIT Awarded Healthcare Specialist Certification
ACP CreativIT has joined the elite group of Healthcare Specialists from Hewlett Packard Inc (HP). To become part of this…
The Powerful End-To-End Emergency Management Solution: HAVRION
In today's world, many organizations are looking for a powerful, end-to-end emergency management solution. Samsung recently partnered with HAVRION, a unified…
Microsoft Teams Is Committed To User Safety
With more end users working remotely than ever, privacy and security are becoming more critical for IT. Microsoft Teams has…

ACP CreativIT and CCCP Announced as Tech Elite 250
ACP CreativIT, formerly known as Arlington Computer Products, was selected as one of the top 250 technology integrators by CRN, a part of…
How do I decide on a premise-based, cloud-based, or hybrid phone system?
Phone systems (VoIP) can be daunting to evaluate. We are here to make that process simple and easy for you…
CCCP Efforts in Light of COVID-19
At ACP CreativIT and Camera Corner Connecting Point, the health and well-being of our customers, employees, and vendors is a…

One simple action you can take to prevent 99.9 percent of attacks on your accounts
-Written by Melanie Maynes, Senior Produt Manager, Microsoft Security. See original post here. There are over 300 million fraudulent sign-in…

Why Pay as You Go Works for SMBs
September 26, 2018, by Michelle Fitzsimmons in Featured, Small & Medium Business (SMB). This article was originally posted here. You’ve…

A Small Part of Something Big
Camera Corner, has grown tremendously in the last 65 years. We’ve been known for our retail store and photo lab…

How to Have a Safe Cyber Summer
Originally posted on Fortinet Blog Written by Anthony Giandomenico | June 27, 2018 Summer means vacations and down time. People are…
Mitel Introduces Integrated Portfolio for the North American Market
Source: UC Today, click here for the original article Mitel, a global leader in the world of business communications responsible for…
Protect Your Bottom Line from Cyber Risks
Originally on Fortinet's blog here. Written by Drew Del Matto. As global cyberattacks persist, cybersecurity is becoming a main focus…

CCCP Adds 8×8 to VoIP Provider Portfolio
Camera Corner Connecting Point announced Nov. 30 it has added unified communications leader 8x8 to its portfolio of VoIP providers.…
Altrusa House of Green Bay
Camera Corner volunteers are picture-perfect! Check out this newsletter from Altrusa House featuring some of our employees. Click here for article.…

Congratulations to Mayville!
Congratulations to Mayville for winning the Quarterback Challenge at the Green Bay Packer’s game! We love being able to give…
Is Your IT Environment Ready For Emerging Technologies?
This article was originally featured on ShoreTel’s website here. WRITTEN BY KATIE KREGEL, DIRECTOR, GLOBAL CORPORATE MARKETING, SHORETEL IT teams…

Congratulations to Green Bay West High School!
Green Bay West High School was awarded $500 for winning the Quarterback Challenge at the Green Bay Packers' game! We…
Camera Corner Connecting Point Recognized for Donation to Beagle Freedom Project
Camera Corner Connecting Point was recognized for its donation of more than $1,800 for the Beagle Freedom Project. Through…
Protect Your Mac
Macintosh computers are very secure and immune from the viruses and malware that affect Windows computers. If you want further…

Ashwaubenon High School awarded $500
Congrats to the Ashwaubenon High School Jaguars on winning the quarterback challenge at Lambeau Field! Through Camera Corner Connecting Point…

Preble High School Awarded $500
Today is an exciting day—we delivered a $500 check to Preble High School for its football program for winning the…

HPE/HP Symposium
Green Bay—Camera Corner Connecting Point held a Symposium with Hewlett Packard Enterprise (HPE) and Hewlett Packard Inc. (HP) Nov. 1,…
VoIP Case Study of Festival Foods
Executing New Initiatives Required a Modern Telephony Solution Elevating the customer experience by treating store guests as part of the…
How a Strong Knowledge Base Supports Top-Notch Service Delivery
Written by Pam Bednarczyk, Content Marketing Manager at ShoreTel Want to increase customer loyalty and overall happiness? Help your customers…
5 Business Scenarios Where SIP Trunking Makes Sense
Written by Pam Bednarczyk, Content Marketing Manager at ShoreTel Cost effective, easy to set-up and scale… if you’re already…
6 Ways Unified Communications Improves Efficiency & Profitability
Time is money. So, how much time / money do your employees spend in meetings? Chances are, it’s more than…
5 Questions To Ask Before Switching To A VoIP Phone System
Implementing a new VoIP phone system is a high-profile project that will impact every aspect of your organization. With stakes…
Customer Experience Management Through Digital Implementation
In today's world it is vital to implement technology in a business's customer experience management toolkit. A total of 88%…
School Security – Your “Must-Have” Checklist
Schools today face a vast assortment of threats, from violence to severe weather, school security needs to protect from all…

Home Invasions Rise with the Temperature
After the long, cold months of winter, most people look forward to the warm relief of summer. With vacations, festivals,…
Creating Better Customer Experiences One Call at a Time
If you make money using the phone, then your phone system needs to be one of your business solutions, not…
10 Ways Your Phone System Improves Your Customers’ Experience
Business competition in today’s economy is fierce. Your customers expect the highest level of customer care, and you and your…
A Phone System that Maximizes Your Control
You’ve realized that your current phone system is no longer working for your growing business. So you do what any…
How Your Phone System Hinders Business Growth
Here’s the good news. Business is booming and you’re ready to grow your employee base to meet the increasing level…
NetAssist Helps Save Lost Data
We love that our NetAssist team can help businesses so much! This is a testimonial from a client who was…
Beware the Latest Version of CryptoWall Malware
A new version of the CryptoWall Malware is making it an even bigger threat to your data. CryptoWall 4.0 has…
Ramping Up: Deploying a Phone System that Works for Remote Employees
What if you were challenged by your CEO to hire a significant number of new employees within the next 6…
The Future of Workforce Communication
When the London Business School hosted its annual Global Leadership Summit in June 2014, the school surveyed attendees about a…
CCCP Featured in Insight Business Magazine
Camera Corner Connecting Point was featured in the April 2014 edition of Insight Business magazine. In the article, CEO Rick…

A Day at Camera Corner Studio
It is 1 p.m. on a Tuesday afternoon and Ryan Chernick, Vice President of Camera Corner Connecting Point’s Managed Services…
Improve Business Transactions With Wireless Networking and Virtualization
CCCP Also Offers VoIP Sales to Enhance Business Communications Convenience and increased productivity due to the ease of mobility are…
Virtual Reality: How to easily establish consistent communications with anyone, anywhere
When the London Business School hosted its annual Global Leadership Summit in June 2014, the school surveyed attendees about a…
How One Business Survived a Potential Data Disaster
Data disaster doesn't always appear as a fire or a flood. The reality is that a greater risk is presented…
Remote Control: How a cloud based phone system prevents stifling remote employee productivity
Imagine for a moment that you’re a sales manager at a growing company and you’ve just been tasked with building…
CCCP’s Networking and Network Monitoring Solutions Invaluable
Company’s NetAssist Department Can Detect and Fix Vulnerable Areas A secure and reliable network is necessary for any business today…
Do You Need IT Consulting or IT Support?
Let Camera Corner Connecting Point's Experts Help Technology and computers are great. Until they're not. When problems arise, or you…
Disaster Recovery and Backup Services — Essential For Your Business
Consider Camera Corner Connecting Point Your Solution Have you ever stopped to think what would happen to your data if…
Problems With Your Network?
Camera Corner Connecting Point’s Managed IT Services Is the Solution If you’re not in the IT business, you know how…
CCCP is Proud to be an Apple and Verizon Dealer
Authorized Apple and Verizon Dealer Camera Corner Connecting Point began in 1953 dedicated to the photography needs of businesses and…
Anti-Fraud Tips From Camera Corner
Implementing anti-fraud measures are crucial for your personal and business safety. We recently had a customer visit our service department…

Meyer Theater Renovation Taking Place on Foundation of Original Camera Corner Location
Exciting renovation plans are in the works for the site of the original Camera Corner Connecting Point - simply Camera…
CCCP is Trusted Technology Source for Green Bay Packers
Once again, Camera Corner Connecting Point is being utilized as a local quality technology center. The Green Bay Packers were…
6 iOS Keyboard Tips Sure To Save You Time
We are in the midst of our big #AppleDays2013 celebration, so I thought you may like a few quick tips…
Mobile Accessibility
[youtube OsMf-eV0VdY] Have you ever wondered what it would be like to work from the comfort of a sandy beach?…
iOS Multitasking Myths
One of the most useful features of iOS, the operating system the runs iPads, iPhones and the iPod Touch, is…
Thank You for 60 Great Years!
Let's take a trip back to 1953. Dwight D. Eisenhower was in office, the New York Yankees won their fifth…

Recent Comments